Password requirements are annoying. There, we said it again.
Do I really need to change my password again?
Didn’t I just change it a few months ago?
How am I supposed to remember my passwords if they need to be so complex?
Preach. We get it. We agree. Complex password requirements annoy us as well.
When we hear the words “cyber security”, the dreaded “Updates to Password Policy” email (cue eye rolls and frustration) comes to mind.
Passwords are a contention point for many organizations.
So why is that?
Problems with password requirements
- 12 Characters
- Alphanumeric
- Must Incorporate 2 or more Special Characters (&%! Etc…)
- No Consecutive Letters
- No Previous Password Reuse
- No Fun
And no wonder people get so fed up with their employer’s password requirements. Doesn’t it just seem like a bit much?
It does seem that way. But there is certainly a method to this password policy madness. There is also a reality where strong password requirements intersect with manageability from an employee’s point of view.
First, we’re learning why those strong password requirements shouldn’t be designed specifically to cause misery. Then, we’re looking at ways password policies can be implemented and enforced effectively.
Avoiding unsecure practices due to password requirements
So, let’s start with some things we wish to avoid as a result of strong password requirements…
- Writing passwords on sticky notes and placing them:
- On your desk
- Under your keyboard
- Directly on your monitor
- Saving all passwords in an unencrypted (unprotected) Excel or Word file
- Saving all passwords in a “Notes” document on your personal phone
- Constantly forgetting these complex passwords and having to reset often
- Stressed out IT departments.
It is possible then, that by enforcing strict password requirements, we create less secure habits. Furthermore we bog down our IT departments with password related issues.
Imagine that, trying to solve one problem, but creating a bigger one.
Humans tend to do this often. But why?
Here’s our take: Humans are, unfortunately, a very impatient species.
Organizations feeling pressure to implement cyber security measures will do so with more emphasis placed on speed than planning. Additionally, our understanding of what makes a strong password is skewed, as described in this lovely comic by xkcd:
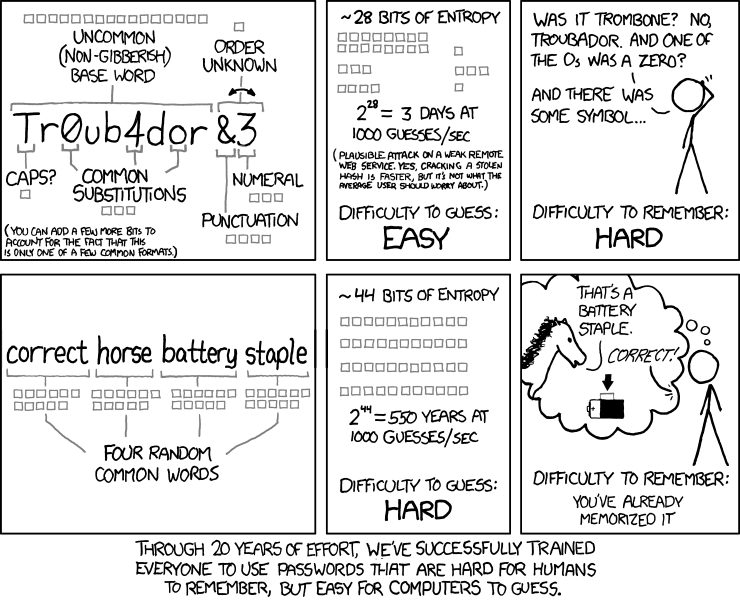
We are also a species of consensus. We accept that 12 characters, alphanumeric, incorporating 2 or more special characters (&%! Etc…), no consecutive letters are what strong passwords require because that’s what everyone else believes makes a strong password.
It is now programmed into our subconsciousness that passwords must be incredibly complex to be secure.
From the standpoint of complexity v. security, we begin to realize we can indeed create strong passwords which don’t require a degree in calculus to memorize.
It just requires a little extra research, and some careful planning. Share the comic above with your IT department and see what they think.
Your users are your customers
Could you imagine knowingly creating a product feature which frustrates your customers? Knowing that each time they use your product, they will develop workarounds to make that feature manageable.
Hopefully that answer is no.
When password requirements are enforced through policy, we must view our employees as internal customers.
Additionally, in thinking this way, we must guide our internal customers and communicate the ways in which they can sustainably manage strict password requirements.
Is this easier said than done? No! It just takes a little more planning and a little more time. Besides, the result of this careful planning means less frustration and more security in our organizations.
Consider this:
When implementing a strict password policy, don’t make the change over a weekend and expect users to embrace this new requirement with open arms when logging in Monday morning.
Talk them through it over time.
Make an announcement at least a month in advance of the new password requirements implementation.
Include in your internal communication:
- Why strong passwords are so important for your organization
- How strong passwords protect the company and individual employees as well
- Tips on creating strong passwords based on your policy and research concerning what a strong password actually is
- Understandable and helpful articles like this one, which describes expert opinions on passwords
If you’re implementing two factor authentication (which you absolutely should), create documentation or share videos describing how to install, setup, and use the technology.
Moreover, if your users frequently use multiple accounts with strict password requirements, please consider providing your employees with a password manager which fits the needs of your organization.
Help out IT!
Make sure whoever manages password issues within your organization (an individual or group or IT professionals) has the necessary resources available when the changeover takes place. Sometimes this just means giving this person or group an open schedule for a few days while password related requests are likely to pile up.
Consider putting your password policy and any related documentation in an easy to find location. Like a shared drive, or on your intranet.
Also, when an employee makes a password related request to your IT department, make sure to always politely refresh their memory concerning where they can find your password policy and helpful password tips.
And if your organization does not have a password policy in place, get that done yesterday.
Should you need help developing understandable, enforceable, and sustainable information security policies, we can help you do that.

