Spend enough time around cyber security folks, and you’re bound to hear about something called Penetration Testing (Pen Testing.)
What is Penetration Testing?
Penetration testing simulates what might happen if a cyber attacker targets your organization. Penetration tests “pen tests” are used to uncover where weaknesses exist in an organization’s information technology systems.
Preferably, these tests are carried out by accredited and skilled cyber security professionals known as penetration testers or ethical hackers.
What is an Ethical Hacker/Penetration Tester?
An ethical hacker is another name for a penetration tester or “pen tester.” An ethical hacker uses the same tools and methods utilized by cyber criminals. However, ethical hackers are good guys trying to help you find cyber security flaws in your information technology systems before the bad guys can find and exploit them. Additionally, you hire a penetration tester if you want to find out where resources should be allocated for cyber security improvements.
As previously mentioned, most legitimate penetration testers hold certifications such as: GPEN, OSCP, GXPN, CEH, CREST, PenTest+, and more. Certifications demonstrate both abilities of the pen tester and their dedication to continuous improvement. When evaluating companies who provide penetration testing, it’s a good idea to ask which certifications their penetration testers hold.
Depending on the skill level of a cyber-criminal, the consequences of being hacked range from minor annoyances to catastrophic interruptions of business processes. Therefore, a good pen tester’s process will range from simple to highly sophisticated hacking methods.
What are the Benefits of Pen Testing?
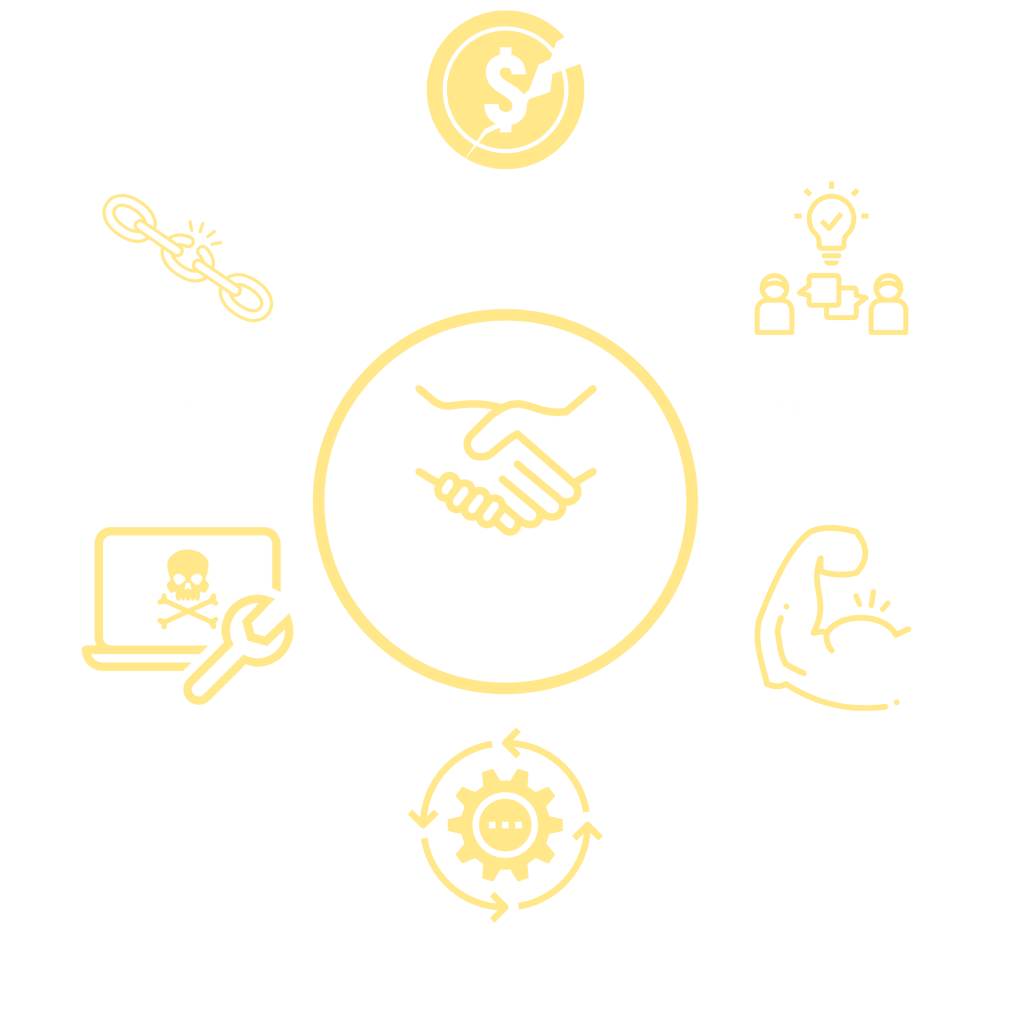
Along with those benefits outlined in the graphic above, this question could elaborate into a whole new blog post. But we will try to keep things concise. After all, you’ve got things to do.
Firstly, penetration testing is the only true test of an organization’s information security systems and procedures. Risk assessments, security gap analysis, or vulnerability scanning helps organizations identify ways to implement cyber security improvements. However, penetration testing identifies the effectiveness of cyber security controls. When we say ‘controls’ we mean anything used to reduce information security risk. So, controls might be firewalls, email filtering, antivirus, network segmentation, security policies and procedures and so on.
Additionally, penetration testing helps you prioritize the weaknesses present in your systems. Without a penetration test, you might uncover a few vulnerabilities by chance and allocate resources to fix them. Although, the vulnerability you uncover might be the byproduct of a larger scale vulnerability which you haven’t identified. Moreover, without an understanding of how critical the vulnerabilities you uncover are, you risk spending time and money fixing the wrong things!
And finally, most importantly, penetration tests help keep your organization safe. For example, what would happen if a cyber-criminal accessed your employee records? How about if a hacker encrypted your systems with ransomware? Or if your website or applications are taken down due to a DDoS attack? The answer: Nothing good.
Pen tests help you fix the flaws which make those attacks mentioned possible. At the very least, corrective actions resulting from penetration testing reduces the likelihood of serious cyber incidents materializing.
What does a Penetration Test Actually Test?
Once you’ve engaged with a company who offers penetration testing services, they will likely walk you through a few options. The process starts by identifying the scope of the test. What do you want tested? Is it an application? A software product? You might have an idea of what you want tested. Conversely, you might not know where to begin.
Here are some tests to consider:
Network Penetration Test
Focused on network infrastructure (firewalls, servers, modems, routers, switches, workstations, printers, network connected devices, etc.) Identifies ways in which an attacker might gain entry through network devices.
Web Application/Service Penetration Test
Focused on web-based applications and services including browsers, eCommerce sites, and any customized web-accessed and connected applications. The penetration tester uses methods which might expose flaws in these apps. Furthermore, if a web application’s security flaws allows a pen tester access… the pen tester will see how far they can get (within the scope of the project and as defined by the rules of engagement.)
Wireless Network Penetration Test
Focused on Wi-Fi and any devices (laptops, phones, tablets, access points, etc.) connected to the wireless network (you will hear the term IoT or “Internet of Things” used with wireless network testing.) A security flaw in only one device, such as a network connected SmartTV or Printer, might be the pen tester’s entry point into the entire network.
Physical Penetration Test
Focused on testing the ease of physically entering the organization. Additionally, examines how well security inside of an organization’s facility prevents unauthorized access to sensitive areas. Do you have locks on the doors? Could a physical penetration tester follow an employee in because they’re holding the door open for them?
Social Engineering Penetration Test
Focused on testing human vulnerabilities. If a social engineering pen tester calls your accounting group acting like your CFO and demanding payment wired to their account, what would they do? Comparatively, if your employees get an infected phishing email which looks like a link to a spreadsheet with everyone’s salary, would they click on it?
What are some Approaches to Pen Testing?
A penetration test is usually conducted under one of the following approaches:
Black Box: Simulates a real external cyber attack. Ideally, the pen tester has no information about the client’s environment, and it’s their goal to break in. Notably, this approach is usually the most time consuming, expensive, and risky.
White Box: A pen tester receives complete access to the client’s environment. This might include the IT infrastructure, source code, application designs and business processes. Ideally, for a White Box test, an organization will provide as much information as possible so that the pen tester conducts a thorough assessment.
Gray Box: As you’ve likely guessed, Gray Box testing is somewhere in between White and Black Box testing. A pen tester knows some information about the client’s systems, but not everything. A Gray Box test is great for organizations interested in understanding what might be at risk should a hacker gain entry into their systems.
Where does a Penetration Tester Start?
Usually, a good pen tester will start their process ONLY when the project is scoped, targets identified and validated, rules of engagement and legal restrictions communicated and agreed, and permissions to test during scheduled times are established.
Moreover, discussions between the contracted party and the organization requesting the pen test should clearly define:
- Location(s) of the test (Including applicable international, state, or local laws)
- Assets/IP Ranges/Domains in Scope
- Risks and Limitations of the Test
- Approach
- Confirmation of Ownership of Tested Assets
- Obligations to 3rd Parties
- Tools Utilized by Pen Tester
- Any Relevant Legal Restrictions/Ramifications
- Start/End Dates
- Communication Plans (Including Emergency Contacts and Incident Handling)
- Sensitive Data Handling
- Status Meeting Cadence
- Reporting Requirements
Once documented, this list becomes the Rules of Engagement (RoE). Also, the RoE serves as the governing document for the penetration test. In the event of a Black Box Test, the RoE clearly defines how a Black Box Test is conducted by the pen tester.
How can I get a Penetration Test?
The search for the right penetration testing service for your organization starts with identifying your needs. If you’re a large organization looking for a multitude of different tests at multiple locations, then a large corporation with pen testing services is likely your best bet.
However, if you’re a SMB, and this is your first pen test or you have a limited scope, there are smaller consulting firms in most cities who provide the service.
Specifically, contact the pen testing company, and ask about their processes, the certifications of their pen testers, and what you get in the pen test report. Altogether, a good pen testing provider will have answers to those questions and will provide you with some additional information about their in-house processes.
Want to get started with a penetration test? Curious if you might benefit from one? Contact LastLine Cyber!