How did a healthcare giant fall prey to Ransomware?
If you were to sit a cyber-attacker down on a morality scale, most, if not all the time, that scale is going to tip over towards the “evil” side. How else can we describe someone who attacks a healthcare system in the middle of a global pandemic for their own gain? Especially when ransomware is concerned.
Ransomware in the wild
In the event you are not aware of this event, one of the largest healthcare giants in the United States, Universal Health Services (UHS), was hit with a ransomware attack on September 27th, 2020. The strain of ransomware, Ryuk, is not new. It was first seen in the wild in 2018 and by 2019 the group had already pulled over $61 million dollars in ransom payments targeting a variety of sectors. Look at that number again. $61 million dollars “stolen” from organizations.
Then on September 27th, Ryuk hits UHS. So, what did this mean for all their locations? Absolute chaos.
Impact of ransomware attack
The attack reportedly impacted all 400 UHS locations, taking 3 weeks for UHS to get all of their systems back up and running. In the meantime, medical staff locked out of critical systems relied on paper records. In the midst of a pandemic, medical professionals were reduced to paper record keeping! This introduces unnecessary difficulties and additional risks regarding patient care.
The outcomes for UHS could have been far worse. The first death tied to a ransomware attack was recently recorded as a system outage severely delayed the patient’s treatment. This is the unfortunate world we live in today. Attackers do not care who they harm, as long as they get their dollar.
The root cause of this cyber attack: Social Engineering
So how did this happen? Well if you want to read a more technical breakdown, Sophos has you covered. However, I would like to borrow one of their graphics and focus, specifically, on one part of it: Box 1 – Phishing Campaign.
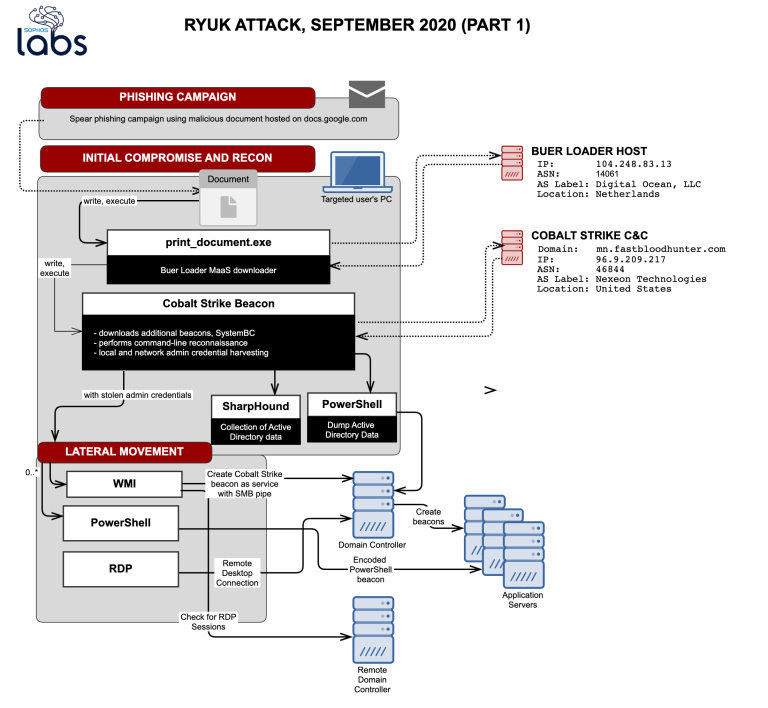
Behind every cyber-attack, well at least 78% of them, phishing is the entry point for the initial compromise. The attackers then try to move laterally through the network from there. This means that at the very beginning of the attack there is a fundamental breakdown of security awareness by an end-user that ultimately leads to the costly and devastating end result. In this case, ransomware.
In some cases, targeted phishing emails are crafted to look very legitimate. However, there are always warning signs with these types of emails.
As I touched upon in my previous blog, a cyber-aware employee base is becoming paramount these days. Users are increasingly targeted, regardless of the company size, and it is extremely important for your employees to be the LastLine (hehe) of defense protecting your company.
The stakes are higher now than they have ever been. The risks are higher now than they have ever been. The capabilities of cyber-attackers are more advanced now than they have ever been.
Don’t think it won’t happen to you. You may be their next target.

